
Firewalls are often the first (and last) line of protection against hackers and cyber criminals. Firewall tips aren’t just box-ticking exercises. They could be the difference between a costly data breach, or stopping dangerous viruses in their tracks.
According to cybersecurity company Fortinet, the average cost of a data breach for small businesses is $3.92 million. There’s also a human cost to cyber breaches, which leaves victims feeling anxious and unsettled. .
That’s why we’ve put this detailed article together – with the ELEVEN best firewall tips to follow.
- What are the best firewall tips for businesses?
- 1. Use a hardware firewall in addition to software
- 2. Keep the firewall software on your device up to date
- 3. Configure the firewall to block all incoming traffic
- 4. Allow only trusted programs and services through the firewall
- 5. Use a firewall with a stateful inspection feature
- 6. Use a firewall with an intrusion prevention system (IPS)
- What is IPS security in firewalls?
- 7. Use a firewall with content filtering
- 8. Use a firewall with application control
- 9. Regularly review and update the firewall rules
- 10. Use strong passwords
- 11. Lean on experts
- Firewall Tips: The Biggest And Most Common Firewall Mistakes
- Firewall Tips: A Conclusion
What are the best firewall tips for businesses?
A study by the cybersecurity company Symantec found that 90% of all cyber attacks target small businesses (preying on the weakness and likely lack of investment in cyber security). The same report states that small businesses are three times more likely to be hacked than large businesses. 👀
Given the scale of cyber criminal activity, firewall software is one of the most important areas for any business to invest in properly.
But the software itself isn’t everything.
Far from it.
You need to follow the right processes and configuration steps to protect yourself and your business as well as you possibly can.
Here are our top ELEVEN firewall tips:
1. Use a hardware firewall in addition to software
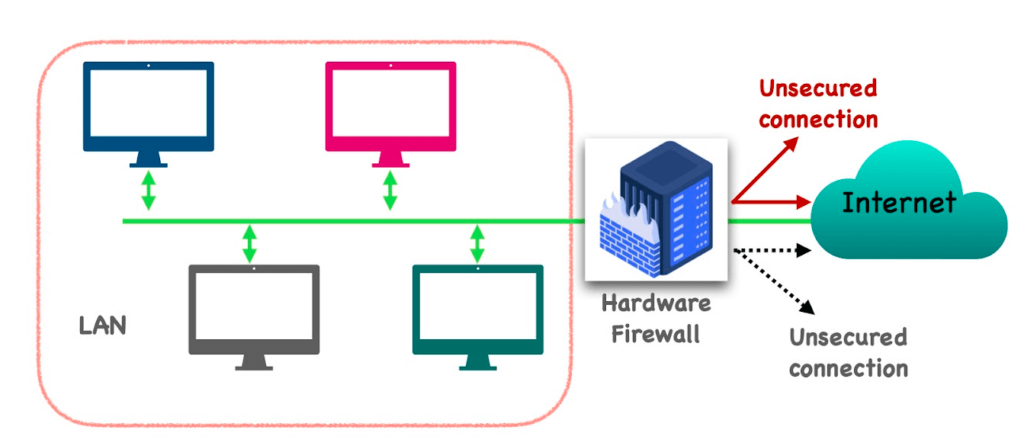
Use a hardware firewall in addition to software. By doing so, you’ll be adding another layer of vital protection.
To explain a little deeper…
A hardware firewall is a physical device. It’s installed between your device, and your internet connection.
With a hardware firewall, you’re physically separating it from other networks. This gives you more control over your incoming and outgoing network traffic.
Not only will this help protect your network from dangerous threats (like unauthorized access, malware, and other terrifying cyber threats), it also allows you to configure a hardware firewall to monitor and block very specific types of traffic.
These include (but are not limited to) incoming traffic from a known malicious IP addresses.
Ultimately, hardware firewalls are valuable for providing an added level of security, and boosting your peace of mind.
2. Keep the firewall software on your device up to date
Nice easy tip this one, but crucial all the same.
First of all, make sure you take time to choose the best firewall software for your situation.
It can vary depending on your status as an individual or business, and other considerations such as budget.
Make sure you are running the latest version of the firewall software to ensure that you have the most current security protection.
Flaws in security software can be costly
Recently, Apple paid a student $100,000 for spotting a flaw in its security software that could be exploited.
Apple quickly issued a new update, but that wouldn’t save anyone who didn’t have their device set to automatically update.
They even ran a PR campaign pointing out how important it was to update the patch.
Firewalls are equally crucial.
Keeping your firewall software updated is so vital because security features need to protect against evolving threats as well as existing ones.
Some cybercriminals (and scammers) are incredibly smart, and they are always developing new and improved techniques for hacking (and exploiting) vulnerabilities.
Software companies release updates to address these issues and protect you – but it only works if you update.
From a non-security standpoint, updates can also result in smoother, faster running systems which take advantage of progress in other areas, giving you more stability and speed on your device.
3. Configure the firewall to block all incoming traffic

Now, our firewall tips are getting into configuration.
But don’t panic!
By default, most firewall software is configured to block all incoming traffic. That’s kind of the point of it.
This helps to prevent unauthorized access to your device and network without you having to understand the software in real depth.
However, there are a few ways to configure a firewall to block incoming traffic.
These depend totally on the type of firewall and the operating system you are using:
- Windows Firewall:
- Open the Control Panel
- Click on “Windows Firewall”
- Click on “Advanced settings”
- In the left pane, click on “Inbound Rules”
- Click on “New Rule” in the right pane
- Select “Custom” and click “Next”
- Choose the protocol and ports you want to block, and then click “Next”
- Choose “Block the connection” and then click “Next”
- Choose when you want the rule to apply and then click “Next”
- Give the rule a name and click “Finish”
- iptables (Linux):
- Open the terminal
- Type “sudo iptables -A INPUT -j DROP” to block all incoming traffic
- To block incoming traffic on a specific port, use this command : “sudo iptables -A INPUT -p tcp –dport [port number] -j DROP”
- Cisco ASA:
- Connect to the CLI of the ASA
- Use the command “configure terminal” to enter configuration mode
- Use the command “access-list [name] deny [source IP address] [destination IP address] [protocol] [source port] [destination port]” to create an access list that denies traffic from the specified source IP address to the specified destination IP address
- Use the command “access-group [name] in interface [interface name]” to apply the access list to the specified interface
Note that these are just examples.
The configuration of firewall software can vary. It really depends on the type of firewall and the operating system you have.
Keep checking, because as things progress, the process might slightly change.
If you’re unsure about configuration or any of these firewall tips then please consult an expert – it’ll be well worth it.
4. Allow only trusted programs and services through the firewall
More configuration firewall tips.
This time, you can be super cautious by configuring the firewall to allow only trusted programs and services to communicate through it.
This helps to prevent malware and other cyber threats from sneaking unsuspected onto your device and network.
Here’s why allowing trusted programs through a firewall is important:
- Better security (obviously). By only allowing trusted programs through the firewall, you won’t totally eradicate the risk, but you will minimize the danger of harmful malware and other malicious viruses getting onto your system to infect it.
- Faster performance: When untrusted programs get through through the firewall, they can significantly slow down your system by using up system resources and network bandwidth. When you only allow trusted programs through, you can often see an uptick in performance and speed. By only allowing trusted programs through the firewall, you can improve the performance of your computer or network.
- Privacy: Any untrusted program can also put your personal information at risk. Having your personal information compromised can cause problems down the line with identity theft and identity fraud, as well as business security risks.
- Tighter compliance: If you are running a business deals with sensitive information, you are likely required to comply with industry regulations (or at least company ones). These often specify that you need strict firewall controls. Trusted programs can help you meet these requirements and ensure greater compliance with industry and company standards.
Only allowing trusted programs through your firewall seems obvious. But it’s a good way of reducing the risk of security breaches while also improving the performance of your device.
5. Use a firewall with a stateful inspection feature
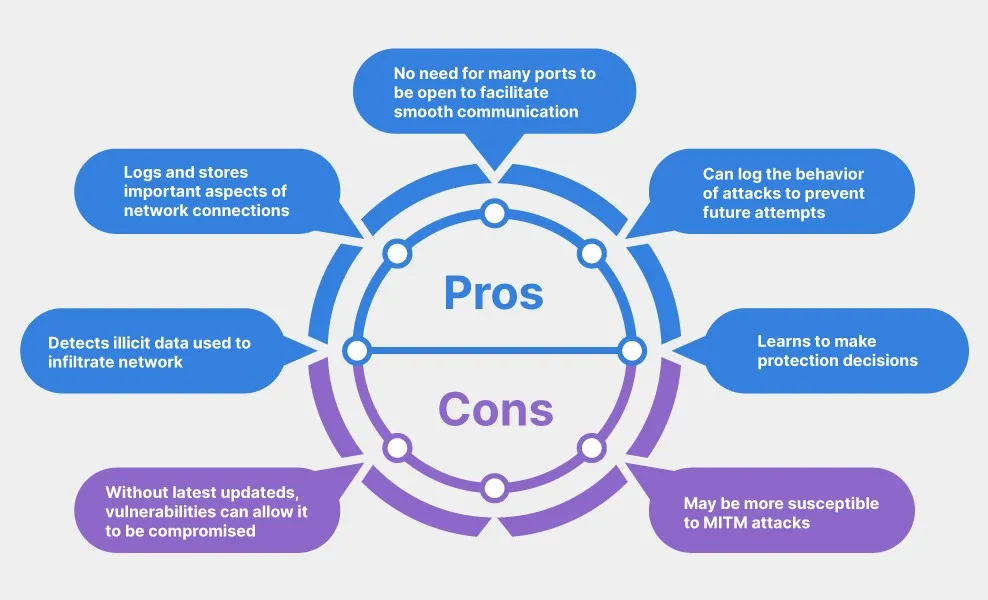
A firewall with a stateful inspection feature is one of our top firewall tips.
It is able to track the state of each connection, and then only allow through traffic that is part of an already established connection.
The benefit of this is that it helps to prevent attacks that aim to sneak in via unused connection points.
But what is it and how does it work?
A firewall stateful inspection feature is a advanced technique used in firewall technology to monitor and control network traffic based on the state of the connection.
This means that the firewall can track the ‘state of a connection‘ – this could be broken down into new or established connections.
From that point, decisions can be made about whether to allow or block traffic, based on the knowledge about the connection state.
It’s different than most traditional firewalls, which often check the packet’s header information, like IP addresses and ports.
A firewall with stateful inspection can track the status of a connection, even if the packets are encrypted. The result of this is a better defence system as there is another decision point.
Stateful inspection firewalls are particularly useful for certain types of attacks.
For example, by keeping track of the number of connections from a single IP address, it can move to block any connections that exceed a certain threshold – therefore indicating possible suspicious activity.
6. Use a firewall with an intrusion prevention system (IPS)
One of the best firewall tips is to use a firewall IPS (Intrusion Prevention System).
It’s an advanced security feature designed to protect you. It can be built into certain firewall products.
Sometimes, it can be added as an additional module.
What is IPS security in firewalls?
An IPS is a security feature that works by analyzing network traffic, live – in real-time. It can then react and help prevent suspicious activity.
How does an IPS work – the different types
An IPS system uses a combination of advanced techniques.
How does signature based detection work
Signature-based detection compares incoming traffic against an already known set of attack signatures. It can then work to blocks any traffic that matches the signatures.
The biggest disadvantage is that this won’t be effective against attacks that are unknown – only those that are already known.
How does anomaly based detection work?
On the other hand, anomaly-based detection, monitors network traffic for abnormal patterns or behaviors. These are ones that specifically deviate from normal network activity.
This is pretty effective against unknown threats, but there is a disadvantage of generating false positives when no threat actually exists.
Behavioral analysis
This is a technique that involves learning the normal behavior of the network. Any deviations would then be identified.
This has the advantage of detecting threats that other methods might not be able to catch. However, it is more complex.
Firewall tips: Use A firewall IPS system
Overall, a firewall IPS system provides a much welcomed additional layer of security.
It can flag and block suspicious traffic all in real time, so it provides better protection against both known and unknown threats.
7. Use a firewall with content filtering
Content filtering is a security feature that allows you to block specific types of content. These can include websites or email messages.
Again, it’s based on predetermined rules, so some setup will be required.
This can be useful for limiting access to inappropriate or malicious content.
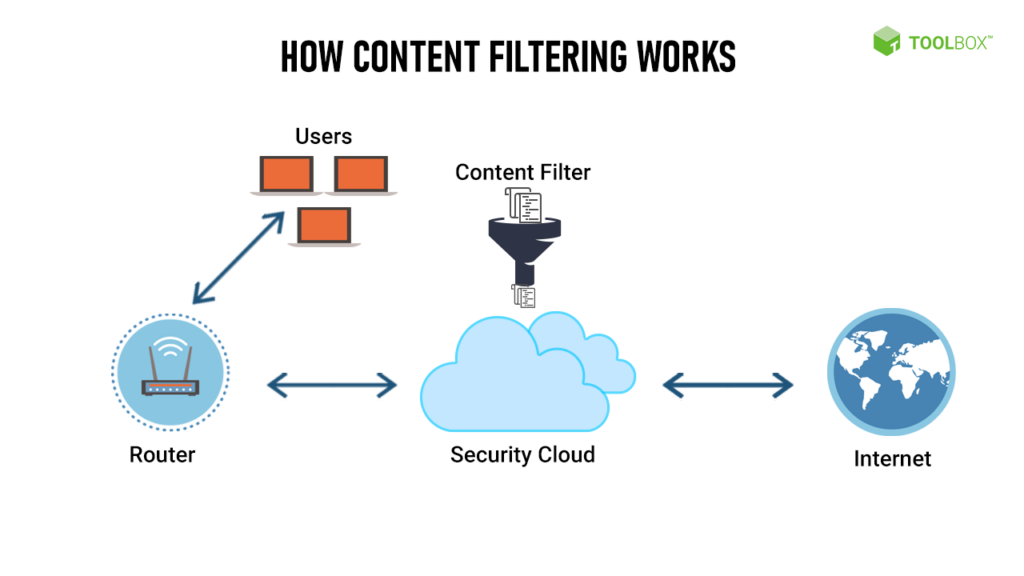
The details behind firewall content filtering
Firewall content filtering is known by several terms, including web filtering or URL filtering.
It allows your firewall tailor access to specific websites or types of content.
The URLs of websites are analyzed, and compared against your rules. If blocked, no access is allowed.
Common usage is to restrict access to adult content and gambling sites.
8. Use a firewall with application control
Application control is a feature that allows you to block specific applications or types of applications from running on your device. This can be useful for preventing malware or other unwanted software from running on your device.
How does Application Control work?
Firewall application control (also known as application filtering or application-aware firewall), is an advanced firewall feature that allows a firewall to control (and monitor) access to specific applications or types of traffic.
The way is works is by analyzing the traffic and identifying the applications that are generating it. After that, it compares them against a set of predefined rules, or an existing database of allowed/blocked applications.
The firewall will deny access if an application happens to be on the blocked list.
9. Regularly review and update the firewall rules
Make sure to regularly review and update the firewall rules to ensure that they are still appropriate for your device and network.
10. Use strong passwords
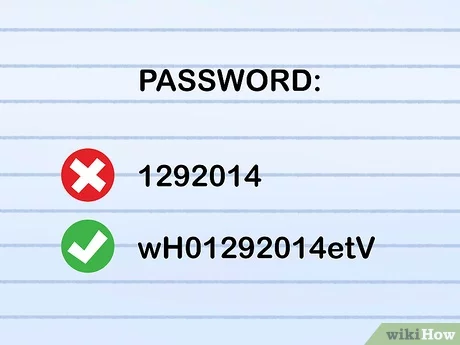
These days it seems like an obvious tip to use strong passwords.
However, for every account that has access to the firewall settings, strong passwords can be the last line of defence.
You need to do everything possible to prevent unauthorized access to your firewall, and that starts with your password.
11. Lean on experts
As with most things tech related, we tend to muddle through. It’s human instinct!
Many of us absently click boxes, and most of the impact is minimal.
With a firewall it’s different – the smallest error in configuration can create weaknesses that others can exploit.
There are a few areas where experts are even more vital – and security is definitely one of them.
Ask for advice and don’t be afraid of asking silly questions if you think it’ll help protect you.
Firewall Tips: The Biggest And Most Common Firewall Mistakes
Unfortunately, there are many mistakes that can be costly when using firewalls. We’ve picked out two of the most common human errors.
1. Failing to keep the firewall software (and hardware) up to date
We’ve talked about both firewall software and hardware.
Put simply, outdated firewall software or hardware can both be vulnerable to brand new threats and attacks. New versions often get rid of security glitches or vulnerabilities.
It’s therefore vital to keep them up to date with the latest patches.
2. Weakening it through improper configuration
Your firewall software might be up to date and have all the latest features…
However, you can still be undone by configuring it incorrectly. It could be something simple like not adding the right websites to content filtering.
The worst mistakes sometimes happen when people switch them off and forget to turn their firewalls back on again, leaving gaps that attackers can exploit.
If you need a firewall expert, find one you trust and ask for help.
Firewall Tips: A Conclusion
Many small businesses will avoid thinking or doing much about their security arrangements, partly through lack of knowledge, and partly because it’s not going to start bringing money through the door.
As a result, most of the action happens post-breach when people panic. 😱
However, we must stress that it is so, so important to pay proper attention to your cyber arrangements, because mistakes can be costly and totally undermine confidence in your business.
To paraphrase an old Chinese proverb… The best time to take firewall tips on board is right at the start.
The second best time is now.
We hope you found this article valuable! For more useful tips, walkthroughs, videos and software recommendations to help kickstart and protect your business, follow us on social @softwarepig.